
Blacklist Management Tool
I have developed a tool for managing the EDL text file, which is stored within the infrastructure-a server and mapped across all Palo Alto firewalls. Two separate tools have been designed for specific tasks: one for uploading and another for downloading. The use case of this tool is to block IP addresses and manage the EDL text file effectively. The reason for developing this tool was that we had a organization using an EDL text file mapped to Palo Alto firewalls to block malicious IPs provided by the SOC team. However, since their infrastructure included many Palo Alto firewalls, manually updating security policies on each firewall was not a practical solution. And the reason behind to create separate tools was, we could not able to transfer files from host PC to the EDL hosted server directly. This tool has been proven effectiveness by reducing significant time that we have to spend by manually updating the list.
To learn more about Palo Alto EDLs click here.
Malicious IP Processor – Upload IP List
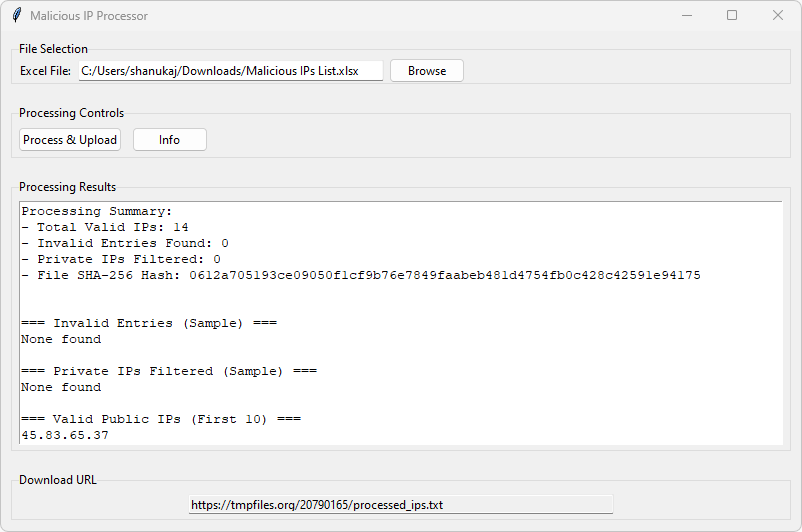
This tool is designed to upload the IP list received from the SOC team for blocking. We need to update the EDL text file with these IPs. The SOC provides the IPs in an Excel sheet with their specific format, and we are required to process the data while ensuring that any private IPs are removed. In the Excel file, the IPs are formatted as 65[.]13[.]66[.]188, so we needed to process the list by removing the square brackets. The tool extracts IPs from the column named “Malicious IPs”. If the column has a different name, we must manually rename it before processing. After processing, the tool will upload the text file to tmpfiles.org via an API and display the download URL. Refer to the following screenshot of GUI of the tool.
The Malicious IP Processor tool includes the following functions:
- Identify and remove any private IPs.
- Process the IP list into a standardized format.
- Convert the Excel file into a text file.
- Upload the file and display its checksum.
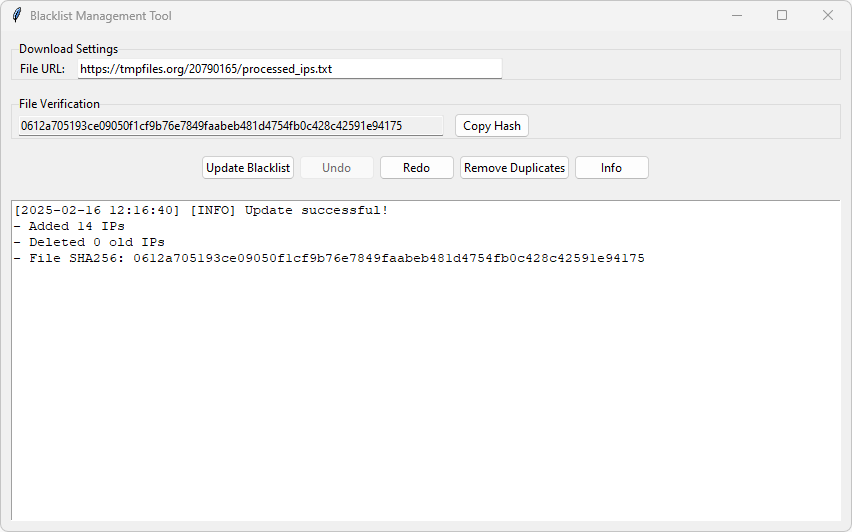
Blacklist Management Tool – Download IP List and Update EDL
The Blacklist Management Tool is used to manage the External Dynamic List (EDL), which contains IP addresses. This tool is hosted on the server and the EDL file location is hardcoded in the tool. After obtaining the upload URL, we must manually enter it here, as direct copying to the server is not possible. We only need to modify the number in the URL field. The URL field always displays in the tool: – Refer to the below screenshot for further understanding;
“https://tmpfiles.org/XXXXXXX/processed_ips.txt“
The tool includes the following features:
- It can maintain an IP limit of 50,000. If the limit is exceeded when adding new IPs, the oldest entries will be removed, making a record of it.
- It does not remove domains from the list—only IP addresses—ensuring effective list management.
- It can remove duplicate IPs, if any exist.
- It supports Undo/Redo functionality for rollback purposes.
Here is the GUI of the Application:
I think this will help you to manage EDL file in your infrastructure also, you only have to change the EDL file path coded in the python script, and make a .exe version of it for the package independency. Since this organization firewalls only supported maximum number of 50,000 IPs in the EDL file, I have capped the maximum number of IPs in the EDL text file to be 50K, check what is the capability of your infra firewalls by referring to the firewall datasheet. – And that’s all.
Here are the GitHub repository link for python code;
https://github.com/shanuka-sandala/custom-tools
We can convert these as .exe file, to do that refer to the following links:
https://www.analyticsvidhya.com/blog/2024/01/ways-to-convert-python-scripts-to-exe-files (btw, I used the 2nd method :D)








Leave a Reply