
Cisco Switch High Memory Utilization Due to pubd Process
We identified an issue where the Cisco switch experienced high memory utilization, causing it to become unresponsive until it was rebooted. This behavior was triggered by excessive memory usage from a process called pubd, which is responsible for communication between the switch and Cisco DNAC. In this article, I will explain how we identified the root cause of the issue and outline the remediation steps taken to resolve it. During the incident, we reviewed the switch’s syslog data to check for any error logs and found the following alerts recurring frequently.
Syslog Alerts:
*Jul 15 09:15:22 10.200.149.172 Jul 15 2025 09:20:50.550 IST: %PLATFORM-4-ELEMENT_WARNING: Switch 1 R0/0: smand: 1/RP/0: Used Memory value 95% exceeds warning level 90%.
*Jul 15 2025 09:41:04.909 IST: %PKI-3-CRL_FETCH_FAIL: CRL fetch for trustpoint DNAC-CA failed
Reason : Enrollment URL not configured.
Cisco Reported Bug: bst.cloudapps.cisco.com/bugsearch/bug/CSCwk90747
To identify which processes were consuming high memory, we executed the following commands at two-hour intervals and compared the output logs. During the comparison, it was observed that the pubd process showed a gradual increase in memory usage over time. Refer to the following outputs from Jul 16 and Jul 17.
Commands used in the Analysis:
show platform software status control-processor brief
show process memory platform sorted
show process memory platform accounting
show platform software process list switch active R0 sort memory
show platform software process memory switch active R0 all sorted
show platform software mount switch active R0
show process memory sorted
show memory allocating-process total
show telemetry internal connection
show telemetry connection all
show logging
Memory processes between Jul 16 and 17 :
Jul 16 :
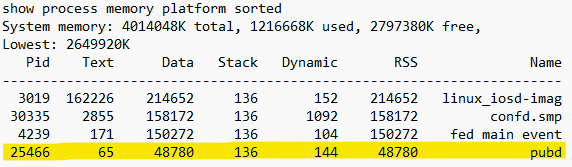
Jul 17 :
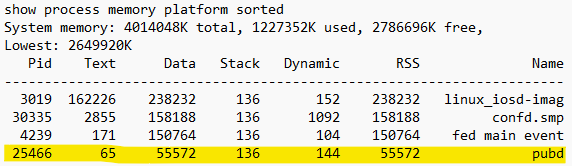
To resolve the issue, there are two steps.
- Upgrade the switch firmware to a fixed version: 17.12.5
- Fix the telemetry connectivity with the DNAC
How to update Cisco Switch from the DNAC:
In this article will show how to address the DNAC connectivity problem with the switch. During the investigation, we discovered that the device’s certificate had expired. To check the certificate status in DNAC, navigate to Provision > Inventory. From there, filter the device using its hostname, IP address, or any of the available filtering options.
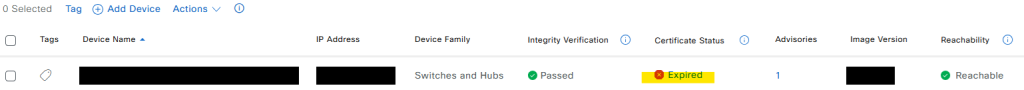
We have the status as expired:
1. To renew the certificate, select the checkbox next to the device, then click the Actions button above the device details view, and choose Update Telemetry Settings.
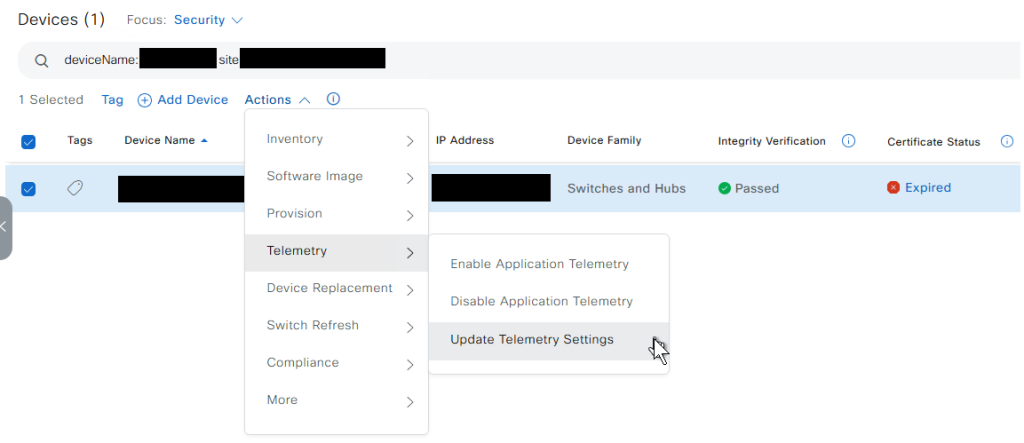
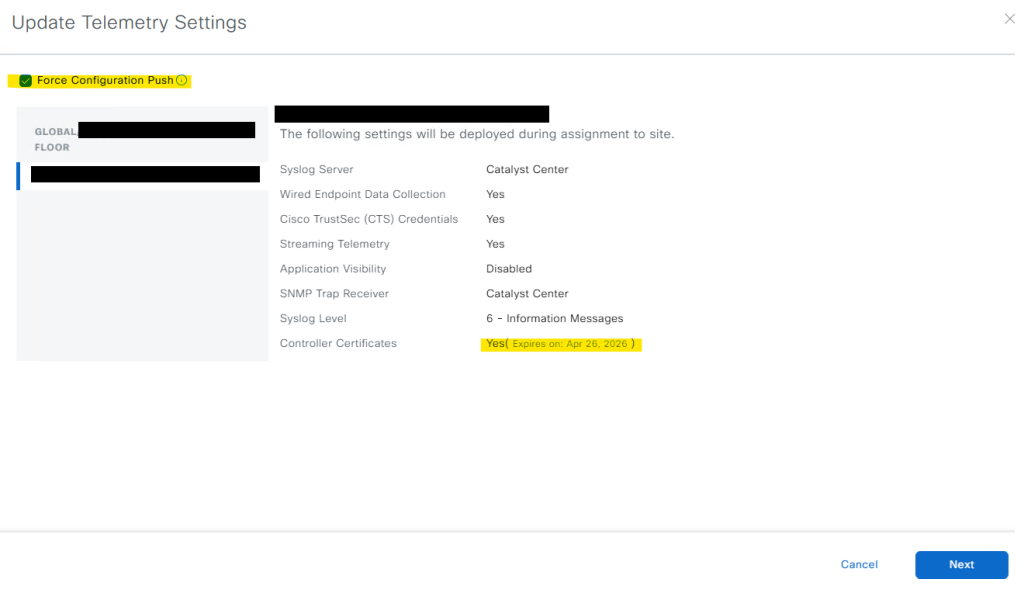
2. After clicking it, a dialog box will appear. In this window, select Force Configuration Push as part of the remediation process. Additionally, review the controller certificate expiry date displayed in the message box.
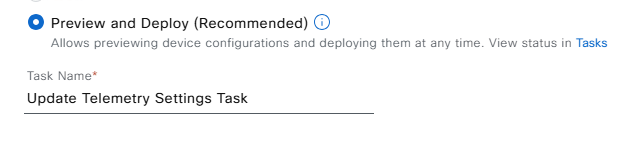
3. After clicking the next select the Preview and Deploy option and click Preview.
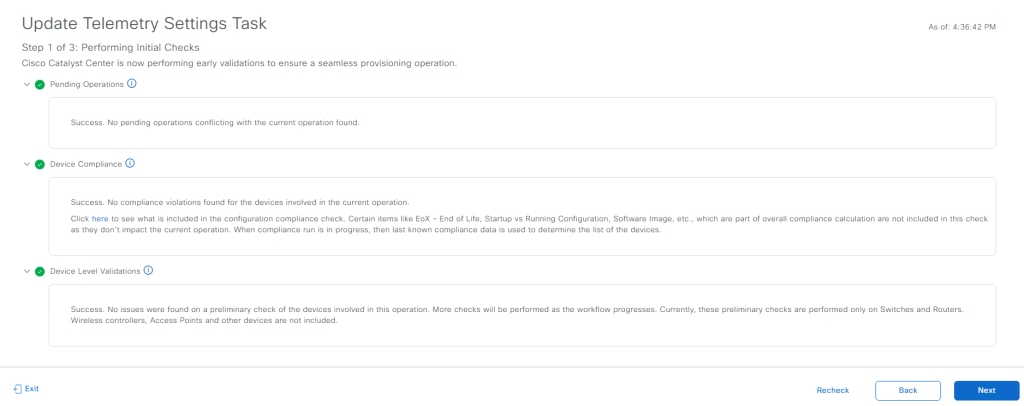
4. On the next page, DNAC will perform initial checks before updating the telemetry settings. Once the validation is successful, click Next to proceed.
5. After clicking Next, a window will appear showing a side-by-side comparison of the configuration to be deployed and the current running configuration of the switch. Review the changes—especially those related to certificate deployment—and then click Deploy to proceed.
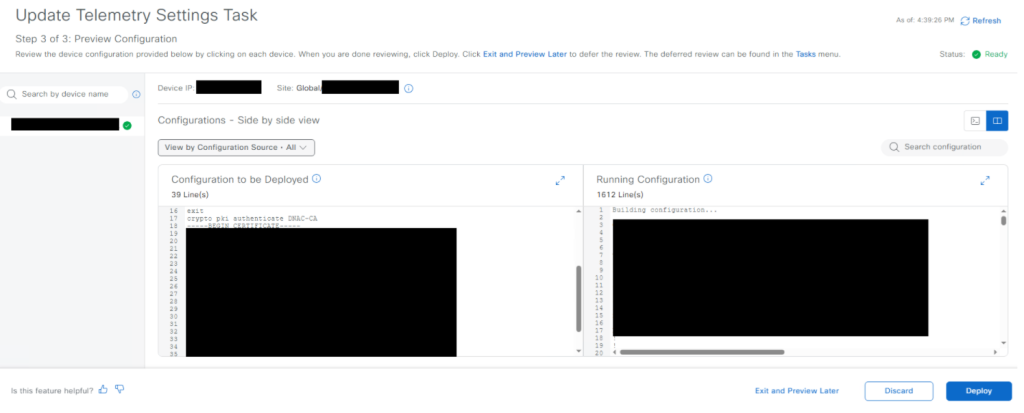
6. After the deployment is complete, verify the telemetry connection on the switch by running the ‘show telemetry connection all‘ command. If the output shows “Connection is up”, it indicates successful connectivity with DNAC. Additionally, it is recommended to check the logs using the ‘show logging‘ command to confirm that the previously observed errors are no longer appearing.
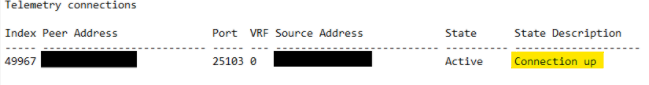
NOTE: We encountered another issue while updating the telemetry settings from DNAC in an environment with a stacked switch. Although the telemetry settings update was reported as successful, the certificate status in DNAC continued to show the certificate as expired, even though the status was marked as “Active.” This issue occurred because DNAC still retained the old certificate for the secondary switch in the stack. To resolve it, we deleted the outdated certificate from DNAC and retried the update. This time, the certificate was successfully applied. During troubleshooting, we also used several options under the Actions menu, including Edit Device to validate credentials and Resync Device to ensure synchronization.
You can verify the pushed certificate by navigating to Menu > System > Settings > Certificates > Device Certificates, and then filtering by the switch’s serial number using the Issued To filter.
Thank you for reading the article, I hope this was helped to fix your issue.






Leave a Reply